Raw Packet VS TCP packet
Sat, Jan 19, 2019Comaparison of Raw Packet VS TCP packet
To send the raw packet I will be using hping.
First create a small file, say a file with just one line “ABCDEF”.
Send this file to another host on raw-IP.
I create a file called task2a.txt and wrote the text “ABCDEF”. I then sent this file twice using hping to the host 192.168.0.116 in raw IP format using -0 switch in a packet with 80 bytes of data.
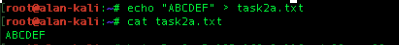
Hping3 Command
Capture it using tcpdump. Use the -X switch to print the load of the packet as you can see the text ABCDEF is in the payload
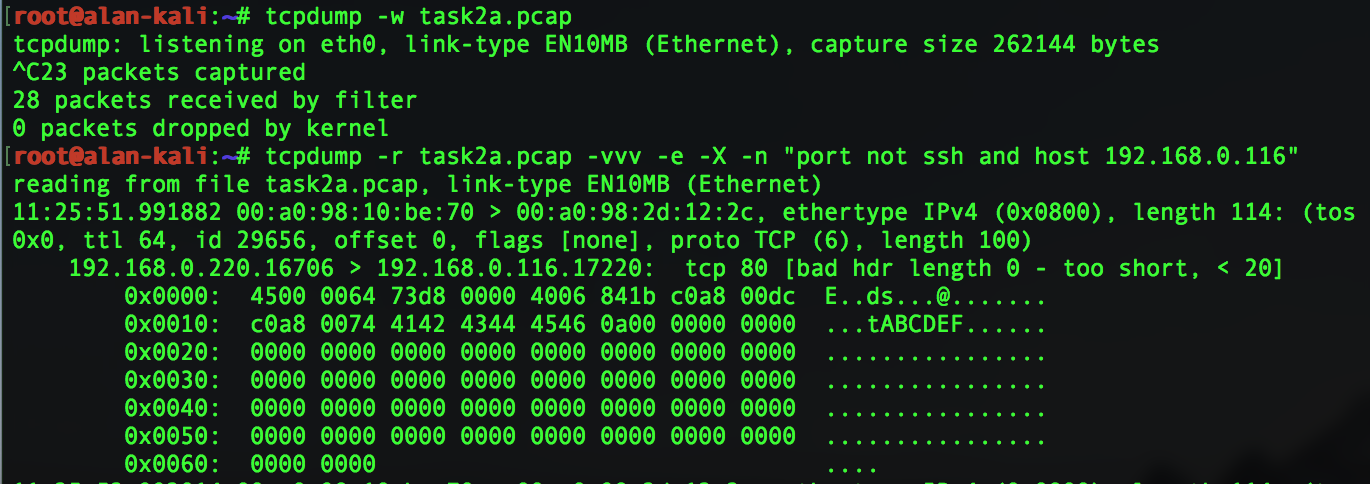
above the first pair of hex 45 is the start of the ipv4 header. This header ends at 74 on the second line. So 45 - 74 is the ipv4 header.
Starting on the frist line the hex set:
4 represents the version and the header length
5 internet header length
00 Type of service
0064 is the total length
73d8 is the id
0 is the flags, all set to 0 in this case
000 is fragment offset
40 is the TTL, 64 in the capture above
06 represents the protocol type, which is 6 for TCP
841b is the checksum
c8a800dc is the scource ipv4 address
c0a80074 is the destination mac address
from 4142 to the end is the Payload
As you can see there was no reply as there was 100% packet loss.
Send the same file over TCP. Again, capture the packet, and view its contents. Compare those with the contents sent above.
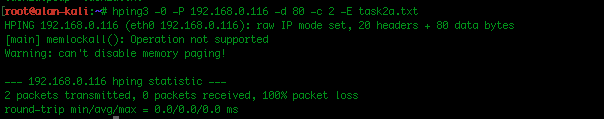
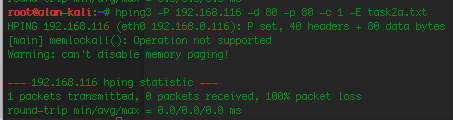
I used the same hping3 command as previously but added destination port but did not use the raw IP flag as hping sends via TCP by default so no need to have any type flags.
Hping command
The fields of the TCP header.
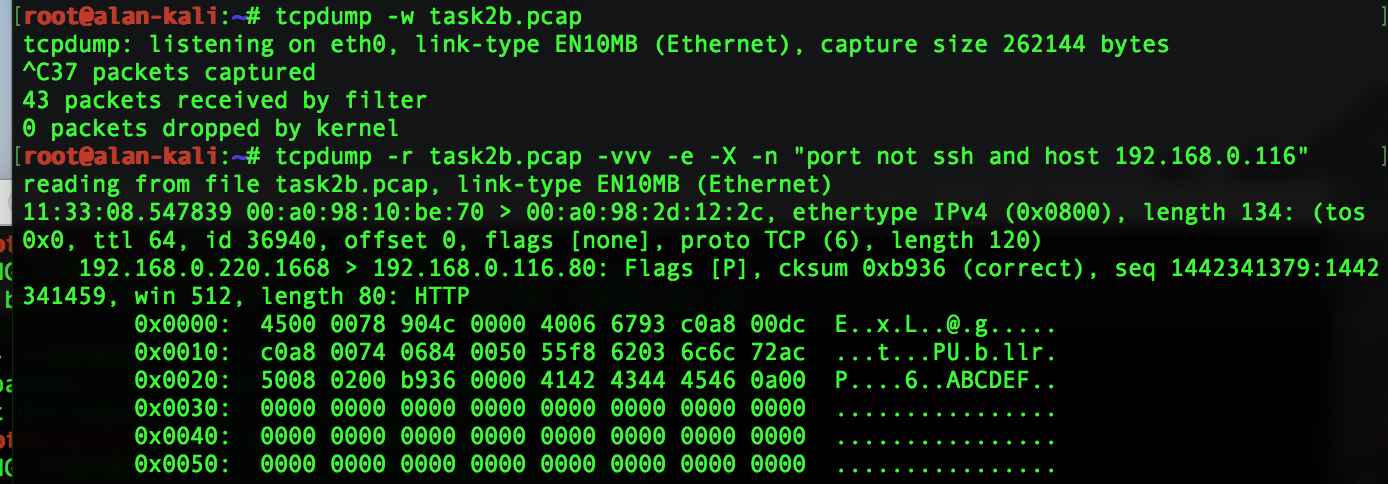
IP Header
above the first pair of hex 45 is the start of the ipv4 header. This header ends at 74 on the second line. So 45 - 74 is the ipv4 header.
Starting on the frist line the hex set:
4 represents the version and the header length
5 internet header length
00 Type of service
0078 is the total length
904c is the id
0 is the flags, all set to 0 in this case
000 is fragment offset
40 is the TTL, 64 in the capture above
06 represents the protocol type, which is 6 for TCP
6793 is the checksum
c8a800dc is the scource ipv4 address
c0a80074 is the destination mac address
TCP header
0684 is the source port which is 1668
0050 is the destination port which is 80
55f8 6203 is the sequence number
6c6c 72ac is the acknowledgment number
5 is the offset
0 is a resevered field
08 is the flags field
0200 is the window field
B936 is the checksum field
0000 is the urgent filed which is bank
from 4142 to the end is the Payload
As you can see there was no reply as there was 100% packet loss.
